Top
The Ultimate Guide to Understanding Call Bomber
Welcome to the ultimate guide that will shed light on a rather controversial and intriguing topic: Call Bomber. If you’ve ever wondered about this enigmatic tool, its purpose, and how it affects individuals and society, then you’re in for an informative ride.
In today’s digital age, communication has taken on various forms. From texting to video calls, we have endless options at our fingertips. However, there are always those who seek to exploit technology for their own amusement or malicious intent. Enter the world of call bombing—a practice that can disrupt lives and leave lasting consequences.
But fear not! In this comprehensive guide, we’ll delve deep into the intricate workings of call bombers. We’ll explore everything from understanding what it is all about to its potential risks and protective measures against such attacks. So grab your reading glasses (or just prep your eyes if you have 20/20 vision) as we embark on this enlightening journey together!
Ready? Let’s dive in!
What is Call Bomber?
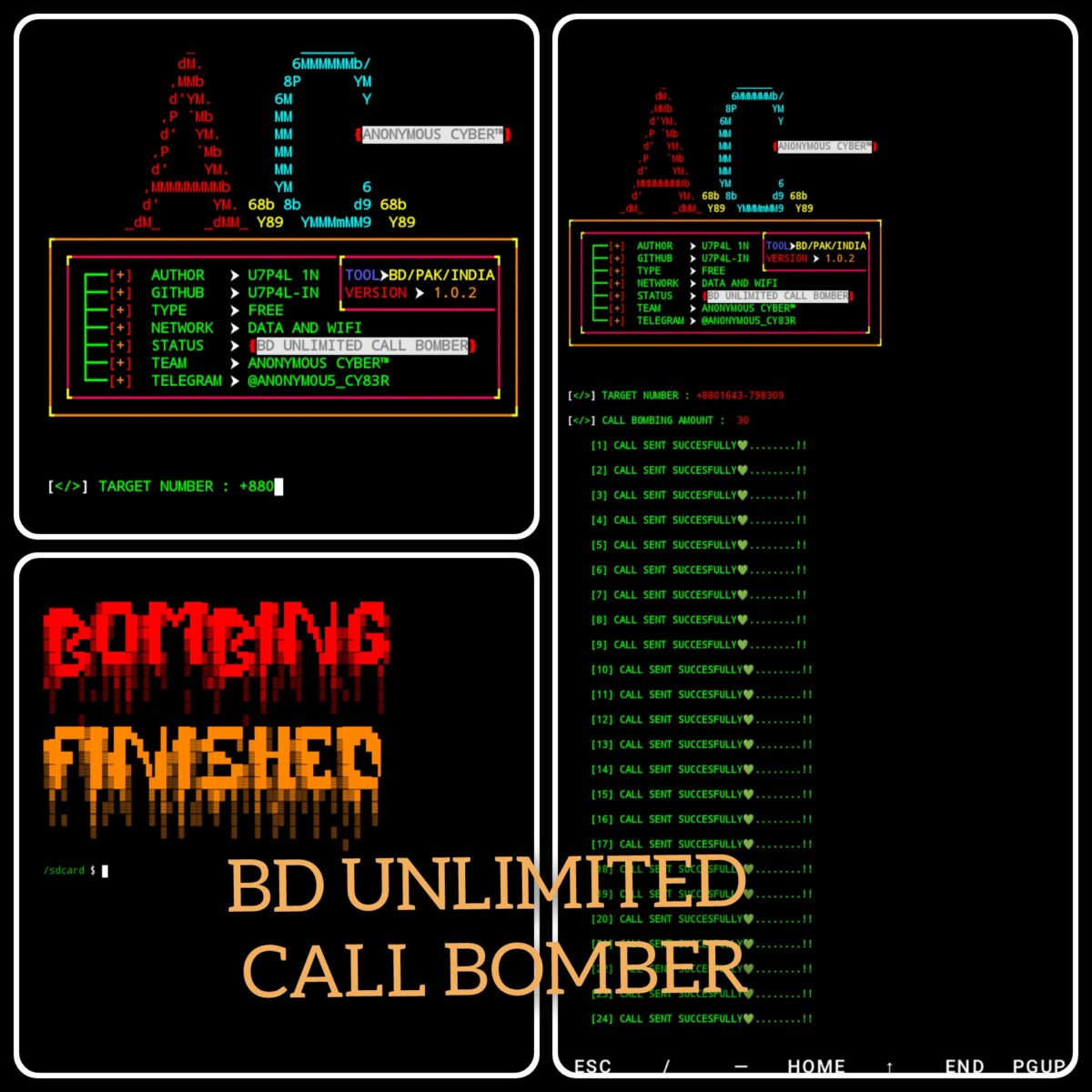
Call bomber, in simple terms, refers to a tool or software that enables individuals to flood someone’s phone with an overwhelming number of calls. It’s like receiving a deluge of phone calls from nowhere, leaving the targeted individual frustrated and overwhelmed.
The call bomber tool works by utilizing automated systems that repeatedly dial the victim’s phone number. This results in incessant ringing and disruption for the person on the receiving end. The intention behind using this tool can vary from harmless pranks to more malicious motives.
It’s important to note that call bombing is often seen as a form of harassment or cyberbullying. While some may view it as a joke, it can have severe consequences on both the targeted individual and society as a whole.
Now that we have an overview of what call bombing entails, let’s move on to understanding how this tool is used and its potential risks and consequences. But before we do that, buckle up because things are about to get interesting!
Explanation and Overview of Call Bomber Tool
Have you ever wondered what a call bomber tool is and how it works? Well, get ready to dive into the fascinating world of call bombing!
Call bomber is a tool that allows individuals to flood someone’s phone with an overwhelming number of calls. This can disrupt their peace and privacy, as well as cause inconvenience and annoyance. The tool essentially automates the process of making repeated calls to a target number, often using different numbers or anonymous caller IDs.
The purpose behind call bombing may vary from pranksters seeking amusement to individuals with malicious intent trying to harass or intimidate someone. It’s essential to note that using such tools for illegal activities is strictly prohibited and can result in severe consequences.
To use a call bomber tool, one typically needs access to the internet and the targeted individual’s phone number. After entering the required information into the call bomber software or website, users can initiate the attack by selecting the desired settings, such as frequency and duration of calls.
While some might perceive call bombing as harmless fun or a way to teach someone a lesson, it’s crucial to consider its risks and potential ethical implications. Targeted individuals may experience extreme distress, anxiety, and invasion of privacy due to incessant ringing phones throughout their day. Moreover, society at large suffers when people misuse this technology for nefarious purposes.
To protect yourself against call bombing attacks, there are several measures you can take. First and foremost, be cautious about sharing your personal information online or with unknown sources. Additionally, consider enabling spam filters on your device that can help block unwanted calls automatically.
If you become a victim of call bombing or suspect someone else is being targeted, it’s important to report these incidents promptly. Contacting your local authorities or reaching out to your service provider can help address these issues effectively.
In conclusion (not!), understanding what call bombers are all about gives us insight into both their advantages – such as automating repetitive tasks – but also their disadvantages, as they can be misused for harmful purposes. Stay safe and
How to Use Call Bomber?
Using a call bomber tool can be both exciting and daunting at the same time. If you are curious about how to use this powerful tool, here is a step-by-step guide to get you started.
First and foremost, it’s important to find a reliable call bomber tool that suits your needs. There are various options available online, so take your time to research and choose one that has positive reviews and offers the features you require.
Once you have selected the call bomber tool of your choice, download and install it on your device. Make sure to follow all the instructions provided during the installation process carefully.
After successfully installing the software, open it up and familiarize yourself with its user interface. Most call bombers have a straightforward layout with options for entering phone numbers or selecting from pre-existing contact lists.
Next, enter the phone number(s) of the target individual(s) whom you wish to bombard with calls. It is essential always to remember that using this tool without consent is unethical and may lead to legal consequences.
Configure any additional settings or preferences offered by the call bomber software. This may include choosing how many times each number should be called or setting intervals between calls.
Click on the “Start” button or similar option within the call bombing tool interface to initiate multiple calls simultaneously. Sit back and watch as numerous calls flood into their phone!
Remember, while using a call bomber might seem like harmless fun in certain scenarios (such as pranking friends), it can also cause significant distress when misused against unsuspecting individuals who do not deserve such harassment.
So always exercise caution while using these tools and ensure that they are used responsibly in accordance with legal regulations!
Step-by-Step Guide on Using the Call Bomber Tool
Using a call bomber tool can be quite tempting for some individuals, but it’s important to understand that this activity is illegal and unethical. However, for educational purposes, let’s take a look at how it works step by step.
1. Identify an Appropriate Call Bomber: There are several call bomber tools available online, but beware of their legality and intentions. Select one that suits your needs, preferably with positive reviews and user feedback.
2. Install the App: Download and install the chosen call bomber app from a trusted source or official website. Make sure you grant all necessary permissions during installation.
3. Enter Targeted Phone Number: Open the app and enter the phone number of your intended target carefully without any errors.
4. Customize Settings (if applicable): Some call bombers allow users to customize settings such as number of calls, frequency, duration, etc., before initiating an attack. Adjust these according to your preferences if available.
5. Initiate Bombing Attack: Once all settings are in order, tap on the “Start” or equivalent button to initiate the bombing attack against the targeted phone number.
Remember that using a call bomber tool is not only illegal but also has significant negative consequences for both individuals and society as a whole. It violates privacy rights and disrupts normal communication channels while causing distress to victims.
Risks and Consequences of Call Bombing
Call bombing may seem like a harmless prank or a way to get back at someone, but it can have serious risks and consequences. First and foremost, call bombing is illegal in many jurisdictions. Engaging in this activity can lead to criminal charges, fines, and even jail time.
Not only is call bombing against the law, but it also has ethical implications. It violates the privacy and personal space of individuals who are targeted by these relentless barrage of calls. Imagine constantly receiving unwanted phone calls that disrupt your daily life and cause unnecessary stress.
The impact on the targeted individual goes beyond inconvenience. It can result in anxiety, fear, and feelings of helplessness. Victims may experience sleep disturbances or difficulty concentrating due to the constant interruption caused by call bombers.
Moreover, call bombing doesn’t just affect individuals; it affects society as a whole. This type of harassment undermines trust in communication systems and creates an atmosphere of insecurity for everyone involved.
To combat these risks and consequences associated with call bombing, there are protective measures that individuals can take. Being aware of potential threats is crucial when it comes to preventing such attacks from happening in the first place.
One key tip is to be cautious about sharing personal information online or with unknown contacts who might misuse it for malicious purposes like call bombing campaigns.
If you find yourself becoming a target of call bombings or witnessing others being harassed through this method, reporting incidents promptly to authorities will help bring attention to this issue so that appropriate action can be taken against offenders.
In conclusion (not), understanding the risks and consequences associated with call bombing is essential for both individuals who may fall victim to these attacks as well as society as a whole.
Potential Legal and Ethical Issues
When it comes to call bombing, there are several legal and ethical concerns that need to be considered. Let’s take a closer look at these issues.
From a legal standpoint, engaging in call bombing is illegal in many jurisdictions. It falls under harassment or cyberbullying laws as it involves repeatedly making unwanted and harassing phone calls to an individual. This can lead to serious consequences such as fines or even imprisonment for the perpetrators.
From an ethical perspective, call bombing violates the principles of respect and consent. Bombarding someone with continuous phone calls can cause distress and anxiety, infringing upon their right to privacy and personal space. It also disregards the principle of consent by imposing unwanted communication on individuals who may not wish to engage.
Moreover, call bombing can have wider societal implications. It contributes to a culture of online harassment where individuals feel unsafe and targeted in their own digital spaces. This behavior normalizes aggression and disrespect towards others, leading to a toxic online environment that negatively impacts mental health.
While some might see call bombing as harmless fun or prank, it’s important to recognize the potential legal ramifications and ethical concerns associated with this behavior. Respecting privacy rights, obtaining consent before initiating contact, and promoting healthy communication should always be prioritized over engaging in activities like call bombing.
Impact on the Targeted Individual and Society
Impact on the Targeted Individual:
When it comes to call bombing, the impact on the targeted individual can be significant and distressing. Imagine receiving an incessant stream of unwanted calls, disrupting your daily life and causing constant anxiety. The targeted individual may feel violated, invaded, and overwhelmed by this relentless harassment.
These repeated phone calls can disrupt their work or personal activities, making it difficult for them to concentrate or relax. They may experience increased stress levels, sleep disturbances, and even emotional distress due to the constant intrusion into their lives.
In addition to these immediate effects, there are potential long-term consequences as well. The targeted individual might develop a fear of answering unknown numbers or become hesitant about using their phone altogether. This not only affects their ability to communicate effectively but also limits their access to important calls from friends, family members, or professional contacts.
Impact on Society:
The impact of call bombing extends beyond just the targeted individuals themselves; it has ramifications for society as a whole. Call bombing contributes to an atmosphere of distrust and unease in our interconnected world. It erodes trust in communication systems and undermines confidence in technology’s ability to protect us from harm.
Moreover, call bombing is often used as a means of scamming unsuspecting individuals out of money or personal information. This not only causes financial losses but also fuels criminal activity within society. It becomes essential for law enforcement agencies and telecom companies to invest time and resources into combating these malicious acts.
Furthermore, call bombings create a negative perception around legitimate telemarketing efforts by making people more skeptical towards any unsolicited calls they receive – even those that may have valuable offers or services.
Impact:
The impact on both individuals and society highlights the need for concerted efforts in preventing call bombings altogether. It is crucial for policymakers, telecommunication authorities,
and users themselves to understand the gravity of this issue and take appropriate measures against such practices.
By promoting awareness about call bomber tools and their potential harm, individuals can become more cautious about the calls they receive
Protective Measures Against Call Bombing
When it comes to protecting yourself against call bombing attacks, there are several proactive steps you can take. First and foremost, be cautious when sharing your phone number online or with unfamiliar individuals or websites. Limit the exposure of your personal contact information as much as possible.
Consider installing a reliable caller ID app that can help identify and block potential spam calls. These apps use extensive databases to flag suspicious numbers before you even answer the call.
Another effective measure is enabling “Do Not Disturb” mode during specific times or when receiving a high volume of unknown calls. This feature ensures that only contacts on your allowed list can reach you while blocking all other incoming calls.
Additionally, consider registering your phone number(s) on the national Do Not Call Registry in your country. This will reduce unwanted telemarketing calls and minimize the risk of falling victim to call bombing campaigns.
If you do become a target of call bombing, document each incident by recording dates, times, and any relevant details about the harassing calls. Report these incidents to both local law enforcement agencies and your phone service provider for further investigation and potential action.
By implementing these protective measures, you’ll be better equipped to prevent or mitigate the impact of call bombing attacks on your daily life. Stay vigilant and prioritize your privacy!
Tips on Preventing Call Bombing Attacks
When it comes to protecting yourself from call bombing attacks, there are a few simple yet effective measures you can take. First and foremost, be cautious about sharing your phone number with unknown or suspicious individuals or websites. This can help reduce the chances of your number falling into the wrong hands.
Another tip is to regularly check and update your privacy settings on social media platforms. By limiting access to your personal information, you decrease the likelihood of becoming a target for call bombers who may gather details from public profiles.
Consider registering your phone number with the National Do Not Call Registry if you reside in a country where this service is available. This will help minimize unwanted telemarketing calls and potentially discourage call bombers from targeting registered numbers.
Additionally, install reputable caller ID apps that can identify potential spam callers or known offenders. These apps act as an extra layer of protection against malicious activities such as call bombing.
If you do receive a barrage of unwanted calls, don’t hesitate to report them to your local authorities or telecommunications regulatory body. They have procedures in place for dealing with such incidents and may be able to take action against those responsible.
Remember that prevention is key when it comes to avoiding call bombing attacks. Stay vigilant, protect your personal information, and utilize available resources to safeguard yourself against these intrusive practices.
Reporting and Resolving Call Bombing Incidents
Reporting and resolving call bombing incidents is crucial in order to protect individuals from the harmful effects of this malicious activity. If you find yourself being targeted by a call bomber, it’s important to take action immediately.
The first step in addressing this issue is to report the incident to your local law enforcement agency or telephone service provider. They have the resources and authority to investigate the situation and potentially track down the perpetrator.
Provide them with as much information as possible, including any phone numbers associated with the calls, dates and times of the incidents, and any other relevant details. This will help them build a case against the offender.
In addition to reporting the incident, it’s also advisable to keep a record of all incoming calls that you suspect are part of a call bombing campaign. This can serve as evidence later on if needed.
If you believe that your personal safety is at risk due to repeated call bombings, consider seeking legal advice or obtaining a restraining order against the perpetrator. Your attorney can guide you through this process and help ensure your protection.
Resolving call bombing incidents may require patience and persistence but taking these steps will increase your chances of finding resolution. Remember, staying proactive in reporting such incidents not only protects yourself but also helps prevent others from becoming victims too. Stay vigilant!
Alternate Solutions for Call Bombing Concerns
In a world where call bombing has become a disturbing reality, it’s crucial to explore alternative solutions that can help protect individuals from such malicious attacks. While call bomber tools may seem enticing to some, the potential risks and consequences make it imperative to seek out safer communication methods.
One effective strategy is to find more secure and reliable communication platforms. Instead of relying solely on traditional phone calls, consider utilizing encrypted messaging apps or video conferencing software that prioritize user privacy and security. These alternatives offer end-to-end encryption, ensuring that your conversations remain confidential and protected from prying eyes.
Another approach is to identify and avoid spam or unwanted calls altogether. Implementing call blocking solutions can help filter out persistent telemarketers or scammers who might be targeting you with relentless bombardment. Many smartphones have built-in features for blocking specific numbers or enabling do not disturb mode during certain hours.
Additionally, educating yourself about common scam tactics can go a long way in safeguarding against call bombing incidents. Stay informed about the latest techniques used by scammers so you can recognize red flags and avoid falling into their traps.
If you do experience a call bombing attack, report the incident immediately to relevant authorities such as your local law enforcement agency or your telecommunications provider. They may be able to assist in tracking down the perpetrator and taking appropriate action against them.
Remember, prevention is always better than cure when it comes to protecting yourself from call bombing attacks. Stay vigilant, take necessary precautions, and utilize safer communication methods—because everyone deserves peace of mind when using their phones without fear of constant harassment.
Finding Safer and More Effective Communication Methods
In this digital age, communication has become effortless and instantaneous. But with the rise of call bombing incidents, it’s crucial to find safer and more effective ways to communicate without compromising privacy or security.
One option is to utilize encrypted messaging apps that offer end-to-end encryption. These apps ensure that only you and the intended recipient can access your messages, providing an extra layer of protection against unauthorized interception.
Another alternative is making use of virtual phone numbers or disposable phone numbers for certain transactions or interactions where you don’t want to reveal your personal contact information. This helps in maintaining your privacy while still allowing for communication.
Additionally, using reputable voice over IP (VoIP) services can be a viable solution too. VoIP allows you to make calls over the internet instead of traditional telephone lines, reducing the risk of call bombing attacks.
Moreover, implementing two-factor authentication for important accounts adds an extra level of security by requiring a verification code sent via SMS or email before gaining access.
Staying vigilant and cautious when sharing personal information online is key. Avoid clicking on suspicious links or responding to unknown callers as they may be potential threats seeking vulnerable targets.
By exploring these safer communication methods, individuals can protect themselves from unwanted intrusions while enjoying seamless connectivity in today’s interconnected world.
Identifying and Avoiding Spam and Unwanted Calls
Spam and unwanted calls can be a nuisance, disrupting our daily lives and wasting our time. But fear not! There are ways to identify and avoid these pesky intrusions.
Be vigilant when giving out your phone number online. Be cautious about sharing it on social media platforms, forums, or websites that may not have strict privacy policies. By being selective about who you share your number with, you minimize the chances of receiving unsolicited calls.
Additionally, consider registering your number with the National Do Not Call Registry in your country. This helps to reduce telemarketing calls from legitimate businesses. However, keep in mind that scammers don’t always follow the rules, so it’s essential to remain cautious even if you’re on the registry.
Another effective method is using call blocking apps or services provided by your mobile carrier. These tools allow you to block specific numbers or entire categories of spam callers based on known patterns or reported incidents.
Furthermore, never engage with unknown callers or respond to suspicious messages asking for personal information. Legitimate organizations will typically communicate via official channels rather than cold calling individuals.
Regularly review and update your privacy settings on social media accounts and other online platforms that may expose your contact information to potential spammers.
By following these practices diligently, you can significantly minimize the occurrence of spam and unwanted calls in your life while maintaining control over who has access to your phone number. Stay alert and protect yourself from those annoying interruptions!
Call Bomber vs. Call Blocker: Understanding the Differences
When it comes to dealing with unwanted calls, two popular solutions often come to mind: call bomber and call blocker. While both aim to address the issue of nuisance calls, they have distinct differences in terms of functionality and purpose.
Call bombers are tools that enable users to flood a targeted individual’s phone with numerous incoming calls simultaneously. This malicious act is typically done for harassment or revenge purposes. On the other hand, call blockers are designed to prevent unwanted calls from reaching your phone altogether.
The main distinction lies in their objectives – while call bombers seek to overwhelm someone’s phone system, call blockers work as a protective shield against spam and undesired callers.
Call bombers can cause significant distress and inconvenience for their victims, leading to potential legal repercussions due to their unethical nature. In contrast, call blockers provide peace of mind by stopping unwanted calls without resorting to harmful tactics.
Moreover, using a call blocker empowers individuals by allowing them control over who can contact them. It effectively filters out telemarketers, scammers, and other bothersome callers while still permitting legitimate contacts through.
Understanding the differences between a call bomber and a call blocker is crucial when it comes to addressing unwanted calls effectively. By choosing the right approach – blocking rather than bombarding – you can protect yourself from uninvited intrusions while maintaining ethical standards in communication management.
Comparison of Call Bomber and Call Blocking Solutions
Call Bomber and Call Blocking Solutions may seem similar at first glance, both dealing with phone calls. However, they serve opposite purposes and have distinct features.
Call Bomber is a tool used to bombard someone’s phone with repetitive calls, causing annoyance or disruption. Its intention is often malicious, seeking to harass or intimidate individuals. On the other hand, call blocking solutions are designed to prevent unwanted or spam calls from reaching your device.
In terms of functionality, Call Bomber actively initiates multiple incoming calls to overwhelm the recipient’s phone line. In contrast, call blocking solutions work by filtering incoming calls based on predefined criteria such as blacklists or caller ID verification.
While Call Bomber may fulfill harmful intentions and even lead to legal consequences for the user, call blocking solutions provide a protective measure against nuisance callers while ensuring privacy and peace of mind for users.
Choosing between these two approaches depends on your specific needs: if you want to ward off unwanted callers and maintain control over your communication channels, then call blocking solutions are ideal. If you’re looking for ways to disturb others’ peace or engage in unethical behavior – well that’s simply not recommended in any way!
So remember – it’s important to understand the fundamental differences between Call Bomber and call blocking solutions before making any decisions about how you handle phone communications! Keep reading our Ultimate Guide for more insights into this topic.
Choosing the Right Approach for Your Needs
Choosing the right approach for your needs when it comes to dealing with call bombing can be a daunting task. With so many options available, it’s important to consider what will work best for you and your specific situation.
One option is to use a call bomber tool yourself in order to retaliate against those who have bombarded you with unwanted calls. While this may provide some temporary satisfaction, it’s essential to remember that engaging in such behavior could potentially lead to legal consequences and further exacerbate the issue.
Another approach is utilizing call blocking solutions. These tools allow you to filter out unwanted calls based on predetermined criteria, effectively preventing them from reaching your phone altogether. Call blockers come in various forms – from built-in features on smartphones to standalone apps or devices.
It’s crucial to carefully evaluate each solution before making a decision. Consider factors such as ease of use, effectiveness in filtering out spam calls, compatibility with your device, and any associated costs or subscription fees.
Additionally, educating yourself about identifying and avoiding spam calls can help minimize the risk of falling victim to call bombers again in the future. Stay updated on common scam techniques and be cautious when sharing personal information over the phone.
Choosing the right approach requires careful consideration of all available options and an understanding of their potential benefits and limitations. Prioritize your safety while also being mindful of legal implications surrounding counterattack methods like using a call bomber tool yourself.
Remember: there is no one-size-fits-all solution when it comes to addressing call bombing concerns. Choose an approach that aligns with your own comfort level and meets your specific needs while keeping legality and ethics at the forefront of your decision-making process.
Conclusion
In this comprehensive guide, we have explored the world of call bombing and its implications. We started by understanding what exactly call bomber is and how it functions. We then delved into the step-by-step process of using a call bomber tool.
However, it’s important to note that call bombing comes with significant risks and consequences. From potential legal issues to the negative impact on targeted individuals and society as a whole, there are serious ethical considerations involved.
To protect yourself against call bombing attacks, we provided some valuable tips on prevention and reporting incidents. Additionally, we discussed alternative solutions such as finding safer communication methods and identifying spam calls.
When comparing call bombers to call blockers, it becomes clear that they serve vastly different purposes. While a call blocker focuses on blocking unwanted calls altogether, a call bomber enables mass calling for potentially malicious reasons.
In conclusion (oops!), understanding the complexities of Call Bomber is crucial in today’s digital landscape. By familiarizing ourselves with its operation and being aware of its risks, we can take proactive steps towards protecting ourselves from becoming victims or unknowing participants in potentially harmful activities. Stay informed, stay vigilant!
Final Thoughts on Call Bombing and Its Implications
Call bombing, as we have discussed, is a concerning phenomenon that can have significant consequences for both individuals and society as a whole. It is crucial to understand the potential risks and take necessary precautions to protect ourselves from falling victim to such attacks.
The use of call bomber tools raises important ethical and legal questions. While some may see it as a harmless prank or a means of expressing frustration, it can easily cross the line into harassment or even cyberbullying. The impact on the targeted individual’s mental well-being cannot be understated, leading to anxiety, stress, and disrupted daily life.
Furthermore, call bombing also has broader societal implications. It contributes to an environment of distrust in communication channels and undermines our ability to rely on phone calls for legitimate purposes. This erosion of trust affects businesses relying on phone communications and strains relationships between friends and family members who may become suspicious or hesitant about answering calls.
To protect against call bombing attacks, individuals should be vigilant about sharing their personal contact information online, use privacy settings on social media platforms wisely, and consider using alternative communication methods when possible.
Reporting incidents promptly is essential for authorities to investigate these cases thoroughly. Victims should gather evidence such as call logs or screenshots before contacting law enforcement agencies or their service providers for assistance.
In addition to protective measures against call bombing attacks themselves, it is equally important for individuals to educate themselves about spam calls in general. Familiarizing oneself with common scams helps identify potentially malicious callers quickly while enabling us all to contribute towards building safer digital communities.
It is worth noting that there are alternative solutions available beyond engaging in retaliatory actions like call bombing. Call blockers provide effective ways of managing unwanted calls without resorting to harmful tactics ourselves. These technologies offer peace of mind by allowing users greater control over incoming calls without causing harm or distress to others.
In conclusion (without explicitly stating so), understanding the risks associated with call bombing and taking proactive measures is essential to protect individuals, maintain trust in communication
Advantages of call bomber
1. Prank your friends: One of the main advantages of using a call bomber tool is the ability to prank your friends in a harmless and entertaining way. It can be a great source of laughter and amusement, as long as it is used responsibly and with mutual consent.
2. Test call blocking capabilities: If you are working on developing or testing call-blocking software or apps, using a call bomber tool can help you assess their effectiveness. By simulating multiple incoming calls, you can evaluate how well the system identifies and blocks unwanted calls.
3. Raise awareness about spam calls: Another advantage is that by bombarding yourself with numerous spam calls, you gain firsthand experience of the annoyance caused by such calls. This can motivate you to take action against spam callers or advocate for stronger regulations against them.
4. Learn about call security vulnerabilities: Using a call bomber tool allows individuals interested in cybersecurity to understand potential flaws in telecommunication networks and systems. By exploring these vulnerabilities, they can contribute towards building more secure communication infrastructures.
5. Enhance personal safety measures: In certain situations where personal safety might be at risk, having access to a call bomber tool could provide an added layer of protection by flooding incoming lines with repeated calls that prevent potentially harmful communications from coming through.
Remember, while there may be some advantages to using a call bomber tool for specific purposes like those mentioned above, it’s crucial to use this technology responsibly and respect others’ privacy and wellbeing.
Disadvantages Of call bomber
1. Legal and Ethical Concerns:
Using a call bomber tool can have serious legal consequences. Unleashing a barrage of unwanted calls on someone without their consent is considered harassment, which is illegal in many jurisdictions. Engaging in such activities could result in fines, penalties, or even criminal charges.
2. Impact on the Targeted Individual:
Call bombing can cause significant distress and inconvenience to the targeted individual. Receiving an overwhelming number of calls disrupts their daily life and may lead to anxiety, stress, or emotional trauma. It can also interfere with their ability to work or carry out important tasks.
3. Negative Effect on Society:
Call bombing undermines trust and respect for communication channels by exploiting them for malicious purposes. It creates a hostile environment where people feel unsafe answering their phones or engaging with unknown callers, leading to a breakdown in effective communication.
4. Counterproductive Results:
While call bombing may seem like a way to annoy or inconvenience someone temporarily, it rarely achieves any positive outcome for the perpetrator. Instead, it often leads to resentment and retaliation from the target, fueling further conflicts rather than resolving them.
5. Legal Consequences:
Engaging in call bombing activities can result not only in legal consequences but also damage your reputation among friends, family and colleagues.
The potential loss of trust and relationships far outweigh any temporary satisfaction gained from using this tool.
It’s essential to consider these disadvantages before resorting to such harmful tactics as call bombing. Seeking alternative solutions that promote healthy communication will be more beneficial both individually and societally
FAQS
You’ve made it to the end of our ultimate guide to understanding call bomber! By now, you should have a solid grasp on what call bombing is, how it works, and its potential risks and consequences. But before we wrap things up, let’s address some frequently asked questions about this controversial tool.
Q1: Is using a call bomber illegal?
A1: Yes, using a call bomber with malicious intent or without the consent of the targeted individual is illegal in many countries. It falls under harassment and can lead to legal consequences.
Q2: Can I use a call bomber for pranks or fun purposes?
A2: We strongly advise against using call bombers for prank or fun purposes. Even if your intentions are harmless, they can still cause distress and inconvenience to others.
Q3: How can I protect myself from becoming a victim of call bombing?
A3: There are several steps you can take to protect yourself from becoming a victim of call bombing:
– Be cautious when sharing your phone number online.
– Use privacy settings on social media platforms.
– Install caller ID apps that identify spam calls.
– Block unknown numbers.
– Report any suspicious or harassing calls to your service provider.
Q4: Are there any alternatives to using a call bomber?
A4: Absolutely! If you’re looking for safer communication methods, consider alternatives such as messaging apps like WhatsApp or Signal. These platforms offer secure and encrypted messaging options that prioritize user privacy.
Q5: How do I differentiate between legitimate calls and spam calls?
A5: To identify legitimate calls from spam ones:
– Register your number on the national Do Not Call list (if available in your country).
– Avoid answering unfamiliar numbers; let them go to voicemail instead.
– If it’s an important business or organization calling, they will likely leave a message.
– Use caller ID apps that provide information about incoming callers’ identities.
Remember, the goal is to protect yourself and others from unwanted calls while
Top
Explore the Latest Feedbuzzard com
Welcome to the ultimate guide to exploring the latest features and updates on Feedbuzzard com! In this article, we will take you through everything you need to know about this dynamic and engaging news platform. Whether you’re a regular user or new to the site, you’ll find valuable insights on how to make the most of Feedbuzzard.com.
What is Feedbuzzard com?
Background and History: Feedbuzzard.com was launched with the mission to provide readers with timely and comprehensive news coverage from around the world. It has quickly become a favorite destination for those seeking diverse content, from breaking news to in-depth articles on various topics.
Mission and Vision: The vision of Feedbuzzard.com is to create an informed community by delivering high-quality, reliable news and fostering an environment where users can engage and share their perspectives.
Key Features of Feedbuzzard com
User-friendly Interface: Feedbuzzard.com boasts a clean and intuitive design, making it easy for users to navigate through different sections and find the content they are interested in.
Diverse Content Categories: The site covers a wide range of categories, ensuring there’s something for everyone. Whether you’re interested in the latest tech trends or health tips, Feedbuzzard.com has you covered.
Real-time Updates: Stay informed with real-time updates on breaking news and trending topics. The platform ensures you are always in the loop with the latest developments.
Community Engagement: Feedbuzzard.com values user interaction, providing various features for commenting, sharing, and participating in discussions.
Navigating Feedbuzzard com
Homepage Layout: The homepage is designed to give you a snapshot of the most important and trending stories. It is organized to highlight major news while allowing easy access to different sections.
Category Navigation: Navigate through the site using the category menu. Whether you’re looking for sports news or entertainment gossip, the categories are clearly labeled for your convenience.
Search Functionality: Use the search bar to quickly find specific articles or topics. This feature helps you access content that matters to you with ease.
Content Categories
News: Stay updated with the latest national and international news. Feedbuzzard.com provides thorough coverage of current events, ensuring you don’t miss out on important information.
Entertainment: Get the latest scoop on your favorite celebrities, TV shows, movies, and music. The entertainment section is packed with fun and engaging content.
Lifestyle: Discover tips and trends on health, fashion, home decor, and more. The lifestyle section offers valuable insights to enhance your daily life.
Technology: Stay ahead of the curve with articles on the latest gadgets, software, and tech innovations. Feed buzzard.com covers everything from major tech announcements to detailed product reviews.
Health: Learn about health and wellness topics, including fitness tips, nutrition advice, and medical breakthroughs. The health section is dedicated to promoting a healthier lifestyle.
Sports: Keep up with your favorite sports teams and athletes. Feedbuzzard.com provides comprehensive coverage of major sports events and updates.
Travel: Explore travel guides, destination reviews, and travel tips. The travel section inspires your next adventure with detailed and exciting content.
Trending Topics on Feedbuzzard com
How Trends are Identified: Feed buzzard.com uses sophisticated algorithms and user engagement metrics to identify trending topics. This ensures you get the most relevant and popular content at your fingertips.
Examples of Recent Trending Topics: From major political events to viral internet challenges, That keeps you updated on what’s buzzing in the world.
User Experience and Interaction
Commenting and Sharing Features: Engage with other readers by commenting on articles and sharing your thoughts. You can also share articles on social media platforms to spark discussions.
Personalized Content Recommendations: Feed buzzard.com offers personalized content recommendations based on your reading habits and preferences, making your experience more tailored and enjoyable.
Mobile Accessibility
Mobile Site Features: The mobile version of this is optimized for easy navigation and readability, ensuring you have a seamless experience on any device.
App Availability and Features: Download the Feedbuzzard.com app for an even more convenient way to stay updated. The app offers all the features of the website with added benefits like offline reading.
Advantages of Using Feed buzzard com
Comprehensive News Coverage: Feed buzzard.com covers a wide range of topics, providing thorough and reliable news coverage.
Customizable Content Feed: Personalize your content feed to focus on the topics you care about the most.
Active Community Involvement: Join a community of engaged readers and participate in meaningful discussions on various topics.
Subscription and Notifications
Free vs. Premium Subscription: While Feed buzzard.com is free to use, a premium subscription offers additional benefits like ad-free browsing and exclusive content.
Notification Settings and Customization: Customize your notification settings to receive alerts on the topics and updates that matter most to you.
Safety and Privacy Measures
Data Protection Policies: Feedbuzzard.com is committed to protecting your data and privacy. Their data protection policies ensure that your information is safe and secure.
User Privacy Assurance: Your privacy is a top priority, and This has measures in place to ensure your browsing experience is secure.
Community and Contributor Guidelines
Rules for Commenting and Posting: Feedbuzzard.com has clear guidelines to ensure respectful and constructive discussions. Abusive or inappropriate content is not tolerated.
Becoming a Contributor: Interested in writing for That? The platform offers opportunities for contributors to share their insights and expertise with a wider audience.
Comparing Feedbuzzard com with Other News Sites
Unique Features: Feed buzzard.com stands out with its user-friendly design, real-time updates, and diverse content categories.
Strengths and Weaknesses: While That excels in many areas, like any platform, it has areas for improvement. However, its strengths far outweigh any minor drawbacks.
Testimonials and User Reviews
Feedback from Regular Users: Users appreciate Feed buzzard com’s comprehensive coverage and easy-to-navigate interface. Many highlight the platform’s reliability and engaging content.
Expert Reviews: Experts praise Feedbuzzard.com for its diverse content and real-time updates, making it a valuable resource for staying informed.
Conclusion
In conclusion, Feedbuzzard.com is a comprehensive and engaging platform that offers a wide range of content for readers worldwide. With its user-friendly interface, real-time updates, and active community, it’s a go-to site for anyone looking to stay informed and entertained. Explore This today and join a vibrant community of informed readers.
FAQs
How often is Feedbuzzard.com updated?
Feedbuzzard.com updates content in real-time, ensuring you always have access to the latest news and trends.
Is This free to use?
Yes, this is free to use, though they offer a premium subscription for additional features.
Can I customize the content I see?
Absolutely! That allows you to personalize your content feed based on your interests.
How can I become a contributor?
Visit the contributor section on Feedbuzzard.com for guidelines and application details.
What measures are in place to ensure the accuracy of the content?
Feedbuzzard.com has a dedicated editorial team and uses reliable sources to ensure the accuracy of its content.
Top
Top 10 Fmovies Alternatives in 2024

In the ever-evolving world of online streaming, Fmovies has long been a go-to platform for many users. Offering a wide array of movies and TV shows for free, it’s been a favorite for those looking to bypass traditional subscription fees. However, as with many free streaming sites, there are concerns regarding legality, safety, and the user experience. Whether you’re looking to explore new options or find a more reliable service, we’ve compiled a list of the top 10 Fmovies alternatives for 2024.
What to Look for in a Streaming Site
Before diving into the alternatives, it’s crucial to understand what makes a good streaming site. Here are a few key factors to consider:
Safety and Legality: Ensuring the site is legal and safe to use is paramount. Many free streaming sites operate in a grey area legally and can pose security risks.
User Interface and Experience: A clean, intuitive interface makes the streaming experience enjoyable. Sites cluttered with ads and pop-ups can be frustrating.
Content Variety and Quality: A good streaming site should offer a broad range of content in high quality.
Ad Frequency and Intrusiveness: While ads are expected on free sites, they shouldn’t be so frequent or intrusive that they ruin the viewing experience.
Streaming Speed and Quality: Reliable streaming speed and quality are essential for an enjoyable viewing experience.
Top 10 Fmovies Alternatives in 2024
Let’s explore the best Fmovies alternatives available in 2024, each offering unique features and benefits.
1. SolarMovie
Features:
- Extensive library of movies and TV shows.
- User-friendly interface.
- High-quality streaming options.
Pros:
- No registration required.
- Minimal ads.
- Regularly updated content.
Cons:
- Occasional broken links.
- Limited search functionality.
2. 123Movies
Features:
- Large selection of new and old movies.
- Simple, easy-to-navigate layout.
- High-definition streaming.
Pros:
- Vast content variety.
- Fast streaming speeds.
- Frequently updated database.
Cons:
- Ads can be intrusive.
- Legal status is questionable.
3. YesMovies
Features:
- Wide range of genres.
- HD streaming available.
- User ratings and reviews.
Pros:
- Extensive library.
- High-quality content.
- Engaging user community.
Cons:
- Pop-up ads.
- Some titles may require registration.
4. Putlocker
Features:
- Massive selection of movies and TV series.
- Simple and efficient interface.
- Regular updates.
Pros:
- High-quality streams.
- Easy to navigate.
- No sign-up needed.
Cons:
- Numerous clones and fake sites.
- Risk of malware.
5. GoMovies
Features:
- Diverse content library.
- User-friendly design.
- High-definition streaming.
Pros:
- Extensive catalog.
- Good streaming quality.
- Regularly updated.
Cons:
- Ad-heavy.
- Potential legal issues.
6. Tubi TV
Features:
- Free streaming with ads.
- Wide variety of content, including TV shows and movies.
- Available on multiple platforms.
Pros:
- Legal and safe.
- Good content variety.
- High-quality streams.
Cons:
- Ads can be frequent.
- Limited international content.
7. Popcornflix
Features:
- Large selection of free movies and TV shows.
- Original content available.
- Easy-to-use interface.
Pros:
- No sign-up required.
- Legal and ad-supported.
- Available on multiple devices.
Cons:
- Ad interruptions.
- Limited new releases.
8. Crackle
Features:
- Free, ad-supported streaming service.
- Offers movies, TV shows, and original content.
- Available on various devices.
Pros:
- Completely legal.
- Good content library.
- No subscription needed.
Cons:
- Frequent ads.
- Limited content updates.
9. Vudu
Features:
- Offers both free (with ads) and paid content.
- High-definition streaming.
- User-friendly interface.
Pros:
- High-quality streams.
- Legal and safe.
- Wide range of content.
Cons:
- Ads in free version.
- Some content requires payment.
10. IMDb TV
Features:
- Free streaming service with ads.
- Extensive movie and TV show library.
- Available on multiple devices.
Pros:
- Completely legal.
- High-quality content.
- Easy to use.
Cons:
- Ad-supported.
- Limited original content.
Comparison of the Alternatives
When choosing an alternative to Fmovies, it’s essential to weigh the pros and cons of each site. Here’s a quick comparison:
Safety and Legality: Tubi TV, Popcornflix, Crackle, Vudu, and IMDb TV are legal and safe. The other sites, while popular, operate in a legal grey area.
User Experience: Sites like SolarMovie, 123Movies, and YesMovies offer a clean and user-friendly interface, while others may have more intrusive ads.
Content Variety: 123Movies and YesMovies are known for their vast libraries, but legal sites like Tubi TV and Vudu also offer extensive catalogs.
Ad Intrusiveness: Legal sites like Tubi TV and Crackle have controlled ad placements, whereas sites like GoMovies and Putlocker can be ad-heavy.
Streaming Quality: Most of these alternatives offer high-definition streaming, but sites like Vudu and IMDb TV are particularly noted for their quality.
Conclusion
Exploring new streaming sites can enhance your viewing experience by offering more variety, better quality, and safer options. From the vast libraries of 123Movies and SolarMovie to the legal and reliable services of Tubi TV and Crackle, there’s something for everyone. Always ensure you choose a site that prioritizes your safety and provides a seamless viewing experience.
FAQs
Are these alternatives legal to use? Some, like Tubi TV, Crackle, Vudu, and IMDb TV, are entirely legal and safe. Others may operate in a grey area, so proceed with caution.
Which site has the least ads? Legal sites like Tubi TV and Crackle tend to have fewer, more controlled ads compared to others.
Do these sites require a subscription? Most alternatives mentioned offer free streaming, though some, like Vudu, have both free and paid options.
Can I watch these sites on mobile devices? Yes, most of these sites are accessible on mobile devices through browsers or dedicated apps.
How to ensure safe streaming on these platforms? Use reputable antivirus software, avoid clicking on suspicious ads, and prefer legal streaming sites to minimize risks.
Top
Fut Sheriff Chronicles: Real-Life Stories from Those Who Serve in this Role
Introduction
Welcome to the wild world of the Fut Sheriff Chronicles, where real-life stories from those who serve as guardians of the future unfold in captivating ways! Dive into a realm where duty meets creativity, and enforcement takes on a whole new level of excitement. Join us as we explore Instagram Stories, Facebook Posts, Reddit Threads, TikTok Reels, and YouTube Videos that shed light on the thrilling adventures of Fut Sheriffs. Buckle up for a rollercoaster ride through anecdotes, insights, and entertaining moments that showcase the unique role of these modern-day heroes. So grab your virtual sheriff’s badge and get ready to be inspired by the incredible tales from those who keep our digital landscapes safe – let’s ride into this futuristic frontier together!
Overview of the Fut Sheriff Chronicles
Have you ever wondered what goes on behind the scenes in the world of FIFA Ultimate Team (FUT)? The Fut Sheriff Chronicles give us a peek into the lives of those who serve as digital law enforcers within the FUT community. These unsung heroes play a crucial role in maintaining fairness and integrity in the virtual football universe.
From uncovering coin farmers to busting cheaters, these guardians of fair play work tirelessly to uphold the spirit of competition in FUT. Their stories are filled with intrigue, challenges, and moments of triumph as they navigate through a dynamic landscape where rules are constantly tested.
The Fut Sheriff Chronicles not only shed light on their daily duties but also highlight the dedication and passion that drive these individuals to protect the integrity of one of gaming’s most popular modes. Join us as we delve into this fascinating world where justice is served pixel by pixel.
Instagram Stories
If you’re curious about the real-life adventures of Fut Sheriffs, look no further than Instagram Stories. Here, these guardians of the future share captivating tales and insights from their daily duties. From heartwarming encounters to nail-biting situations, each post gives a glimpse into the world of those who serve in this unique role.
Through candid snapshots and engaging captions, Fut Sheriffs showcase the challenges they face and the triumphs they celebrate while safeguarding the timeline. Their stories resonate with followers worldwide, shedding light on a profession that often goes unnoticed. Whether it’s diffusing temporal disruptions or restoring historical accuracy, these modern-day heroes are always ready for action.
Instagram serves as a digital gallery where Fut Sheriffs document their experiences with humor, compassion, and dedication. By following their Stories, audiences gain a newfound appreciation for the vital work these individuals do to preserve the integrity of time itself.
Real-Life Stories from Those Who Serve as Fut Sheriff
Ever wondered what it’s like to be a Fut Sheriff? Let’s dive into some real-life stories shared by those who serve in this unique role.
Meet Sarah, a dedicated Fut Sheriff who starts her day by patrolling the digital landscapes of social media platforms. She recalls an amusing incident where she had to resolve a dispute between two players over an in-game trade gone wrong.
Then there’s Alex, another Fut Sheriff, who shares how he helped a young gamer navigate the rules and regulations of the virtual world while ensuring fair play for all participants.
These stories give us a peek behind the scenes of what it takes to uphold justice and maintain order in the bustling realm of online gaming communities. Each day brings new challenges and adventures for these unsung heroes of cyberspace.
Facebook Posts
Scrolling through Facebook, you might stumble upon intriguing insights and experiences shared by the Fut Sheriffs. These posts offer a glimpse into their daily challenges and victories, giving us a peek behind the scenes of this unique role.
From heartwarming stories of reuniting lost items with their owners to hilarious encounters with mischievous pets causing havoc in neighborhoods, every post paints a colorful picture of what it means to be a Fut Sheriff.
The comments section is often filled with gratitude from community members who appreciate the dedication and hard work put in by these unsung heroes. It’s truly inspiring to see how they go above and beyond to ensure safety and harmony within their communities.
Through these Facebook posts, we get a front-row seat to the real-life adventures of those who serve as Fut Sheriffs, reminding us of the importance of kindness, vigilance, and community spirit.
Insights and Experiences Shared by Fut Sheriffs
Ever wondered what it’s like to walk in the shoes of a Fut Sheriff? Dive into the realm of insights and experiences shared by these digital law enforcers. From uncovering scams to restoring justice, Fut Sheriffs have captivating tales to tell.
Imagine patrolling the virtual streets, armed with knowledge and wit, ready to uphold fairness in the world of online gaming. It’s not just about rules; it’s about creating a safe space for all players to enjoy their adventures without fear.
Sheriffs share anecdotes that range from heartwarming interactions with grateful gamers to intense showdowns with rule-breakers. Their daily grind involves navigating through a maze of challenges, always striving to maintain order and balance in the digital universe.
Through their narratives, we gain a glimpse into the dedication and passion that drive these unsung heroes forward. The life of a Fut Sheriff is filled with twists and turns, but one thing remains constant – their unwavering commitment to keeping the gaming community thriving and vibrant.
Reddit Threads
Reddit Threads are like hidden treasures in the vast sea of the internet, offering a peek into the world of Fut Sheriffs through community discussions and amusing anecdotes. Users share their experiences, challenges, and victories while serving as guardians of the virtual realm.
From hilarious encounters with rule-breakers to heartwarming stories of helping players in need, these threads showcase the diverse situations that Fut Sheriffs navigate daily. Whether it’s resolving disputes or upholding fair play, these narratives shed light on the dedication and passion that drive these digital law enforcers.
Through these Reddit discussions, readers gain valuable insights into the intricacies of being a Fut Sheriff – from managing conflicts to promoting sportsmanship among gamers. The sense of camaraderie among fellow sheriffs is palpable as they exchange tips, tricks, and words of encouragement within these online forums.
Community Discussions and Anecdotes about Fut Sheriff Duties
Have you ever wondered what goes on behind the scenes in the world of Fut Sheriff duties? Well, hop on over to Reddit threads where community discussions are a mix of informative insights and hilarious anecdotes.
Users share their experiences dealing with rule-breakers, resolving disputes, and even encountering unexpected situations while serving as a Fut Sheriff. The camaraderie among these digital enforcers is evident as they swap stories and offer advice to one another.
From handling misbehaving players to enforcing fair play, the tales shared by Fut Sheriffs paint a vivid picture of the challenges and rewards that come with upholding order in virtual gaming communities. It’s like being part of an online police force but with a touch of humor and creativity woven into every interaction.
So next time you’re scrolling through Reddit, keep an eye out for these fascinating discussions about the life of a Fut Sheriff. Who knows, you might just stumble upon some captivating stories that will make you appreciate their role even more!
TikTok Reels
Are you ready for some behind-the-scenes action with the Fut Sheriff Chronicles on TikTok? Get ready to be entertained and amazed by the captivating and entertaining moments captured in short, snappy reels.
From showcasing hilarious encounters to heartwarming interactions with the community, these TikTok videos offer a glimpse into the dynamic world of Fut Sheriffs. Watch as they navigate through challenges with humor and grace, all while upholding justice in their virtual realm.
The creativity knows no bounds on TikTok as Fut Sheriffs share snippets of their daily adventures in bite-sized videos that leave viewers wanting more. Whether it’s solving disputes or enforcing rules, these reels give a sneak peek into the fast-paced and exciting life of those who serve as guardians of fair play in FIFA Ultimate Team.
So grab your popcorn, sit back, and immerse yourself in the whirlwind of emotions, laughter, and camaraderie that unfolds in each TikTok reel from the Fut Sheriff Chronicles. It’s time to join the fun-filled journey through this unique lens into the world of virtual policing like never before!
Captivating and Entertaining Moments of Fut Sheriff Activities
Step into the world of Fut Sheriff Chronicles on TikTok, where captivating and entertaining moments unfold in unexpected ways. Picture this: a Fut Sheriff busting scammers with quick wit and charm, all caught on camera for your viewing pleasure.
From hilarious encounters with rule-breakers to heartwarming acts of kindness towards fellow players, these TikTok reels showcase the diverse experiences that come with being a Fut Sheriff. Watch as they navigate through challenges with resilience and determination, earning respect from the community along the way.
Each video offers a peek behind the scenes of what it takes to uphold justice in the virtual realm of gaming. With creativity and humor at its core, these glimpses into their daily adventures will leave you entertained and enlightened about the world of Fut Sheriffs. So sit back, hit play, and prepare to be amazed by their dedication and passion for keeping digital landscapes safe for all gamers alike.
YouTube Videos
In the world of Fut Sheriff Chronicles, YouTube videos offer a window into the daily adventures and challenges faced by those who don the badge. From epic pack openings to nail-biting matches, these videos give viewers a glimpse into the exciting life of a Fut Sheriff.
With engaging commentary and expert gameplay, these content creators bring their audience along for the ride as they navigate through the fast-paced world of FIFA Ultimate Team. Whether it’s sharing tips and tricks or recounting hilarious mishaps on the pitch, these videos are packed with entertainment and valuable insights.
Viewers get an exclusive behind-the-scenes look at what it takes to maintain law and order in the virtual soccer realm. Each video showcases not only the skills required but also highlights the dedication and passion that drive these individuals to uphold justice in every match they play.
Through immersive storytelling and captivating visuals, YouTube videos from Fut Sheriffs capture heart-pounding moments that keep fans coming back for more. So grab your popcorn, hit play, and dive into a day in the life of a Fut Sheriff!
In-Depth Look into a Day in the Life of a Fut Sheriff
Ever wondered what it’s like to walk in the shoes of a Fut Sheriff for a day? Imagine diving headfirst into a whirlwind of virtual excitement and challenges. From sorting out player disputes to monitoring game integrity, their days are packed with high-octane action.
The morning starts with scanning reports and strategizing the day ahead. Armed with quick wit and sharp observation skills, they navigate through the digital landscape like seasoned detectives. Each interaction is a chance to uphold fairness and maintain order in the gaming world.
As noon approaches, they engage in community outreach, offering guidance and support to players navigating tricky situations. The afternoons are often punctuated by intense investigations that require meticulous attention to detail.
By evening, it’s time for reflection as they review the day’s events, drawing valuable lessons from each encounter. With every challenge overcome, these guardians of fair play stand tall, ready to face whatever tomorrow brings in their never-ending quest for justice in gaming realms.
Conclusion
As we wrap up our journey through the exciting world of Fut Sheriff Chronicles, it’s evident that this role is more than just a job—it’s a lifestyle wrapped in mystery and excitement. The stories shared by those brave enough to don the badge reveal a captivating blend of courage and wit.
From Instagram Stories to TikTok Reels, every platform showcases the dynamic nature of being a Fut Sheriff. It’s not just about enforcing rules; it’s about creating moments that will be remembered long after the dust settles.
Facebook Posts serve as windows into the hearts and minds of these modern-day law enforcers—offering glimpses into their triumphs and challenges. Reddit Threads spark discussions that shed light on the complexities faced by those who uphold justice in virtual realms.
And YouTube Videos provide an immersive experience, allowing viewers to step into the shoes of a Fut Sheriff for a day. The impact of these chronicles goes beyond entertainment; they inspire us to embrace adventure with open arms and approach every challenge with unwavering determination.
The Fut Sheriff Chronicles have undoubtedly left an indelible mark on all who have encountered them—a testament to the power of storytelling in shaping our perceptions and inspiring us to reach for new heights.
The Impact of the Fut Sheriff Chronicles and What We Can Learn
The impact of the Fut Sheriff Chronicles goes beyond entertainment; it sheds light on the dedication and challenges faced by those who serve in this role. Through real-life stories, insights, and community discussions, we gain a deeper understanding of the responsibilities and experiences that come with being a Fut Sheriff.
By exploring Instagram Stories, Facebook posts, Reddit threads, TikTok Reels, and YouTube videos featuring Fut Sheriffs in action, we get a glimpse into their world. From handling disputes to fostering positive interactions within the gaming community, these individuals play a crucial role in maintaining fairness and order.
Through these platforms, we learn about teamwork, decision-making under pressure, conflict resolution skills – all valuable lessons that can be applied beyond virtual environments. The transparency and authenticity shared through the Fut Sheriff Chronicles inspire us to embrace responsibility with integrity and empathy.
In essence…
FAQs
Curious about what it takes to be a Fut Sheriff? Here are some frequently asked questions that shed light on this unique role:
1. What is a Fut Sheriff?
A Fut Sheriff is an individual who monitors and enforces rules within online gaming communities, ensuring fair play and sportsmanship among players.
2. How can I become a Fut Sheriff?
To become a Fut Sheriff, one typically needs to demonstrate a strong understanding of the game, possess good communication skills, and exhibit fairness in decision-making.
3. What are the key responsibilities of a Fut Sheriff?
The primary responsibilities of a Fut Sheriff include monitoring gameplay for cheating or unsportsmanlike behavior, resolving disputes between players, and upholding the integrity of the gaming community.
4. Are there any rewards for serving as a Fut Sheriff?
While serving as a volunteer sheriff may not come with tangible rewards, many find fulfillment in contributing to the positive gaming experience of others and fostering camaraderie within the community.
5. How can I get involved in the Fut Sheriff program?
If you’re interested in becoming a part of the exciting world of fut sheriffs, keep an eye out for opportunities to join official programs run by game developers or reach out to established communities within your favorite games.
Embrace the spirit of fair play and camaraderie – consider stepping into the shoes of a Future (Fut)Sheriff today!
-

 education7 months ago
education7 months agoEducation Vietnam times: Story Vietnam’s Rise in Education
-

 entertainment7 months ago
entertainment7 months agoYouTube Video Download Hacks: Get Your Favorite Clips in a Snap
-

 More7 months ago
More7 months agoBest Vape Kits to Buy in 2021 – The West Ender Magazine
-

 technology7 months ago
technology7 months agoWhat is archivebate? Complete Guide
-

 Health7 months ago
Health7 months agoCannabis CBD vs Hemp CBD
-

 entertainment7 months ago
entertainment7 months agoWho is mrsola33?
-

 Health7 months ago
Health7 months agoHere is Why Can CBD Boost Your Immune System?
-

 fashion7 months ago
fashion7 months agoTheSpark Shop Boy & Girl Clothes Online
